
Process Risk & Controls (PRC)
Identify Process Risks, Design, Implement and operate effective controls to mitigate Risks to
your organization and customer Information & Technology Assets.

Process Risk & Controls
Process Risk & Controls (PRC) is a structured method that helps an organization to evaluate, understand, and optimize their business processes, which is important to promote risk management to mitigate business risks. With PRC, an organization can check the health of their operational activities, financial reports, and their compliance with its internal procedures, as well as operate in compliance with operational regulations under the law.
Identify Risks in Business Processes and Workflows
Unlock the Potential of Your Business Processes
We specialize in providing comprehensive business process analysis and workflow diagram services tailored to your business requirements. Our unique approach will help identify inherent risks, and streamline your business processes for efficiency to protect critical information used in your processes. Optimized and secure processes can lead to significant cost savings in the long term.
Process Optimization, Operational Risk and Controls
Our Virtual CISO Services brings a wealth of knowledge in both operational risks and cybersecurity, ensuring your business processes are both effective and secure.
Get Started Today
Knowing your business processes are efficient and secure lets you focus on what you do best – growing your business. Ready to transform your business processes? Contact us for a free consultation and take the first step towards a more efficient and secure business operation.

Prepare your SaaS Business for Cyber Incidents
We provide Incident Response Planning & Testing (IRP)-as-a-Service
Incident response and management are considered essential minimize the damage of a Cybersecurity Incident or Outbreak. An IRP (Incident Response Plan) with Testing Services is a critical facet to protect and ensure continuity of your business operations, data and customers.
Preparation
Detection & Analysis
Containment, Eradication, Recovery
Post-Mortem
IRP Service Objectives
The objective of our Incident Response Plan (IRP) Service, is to help your business:
- Limit immediate incident impact to customers and business partners
- Recover from the incident
- Determine how the incident occurred
- Find out how to avoid further exploitation of the same vulnerability
- Avoid escalation and further incidents
- Assess the impact and damage in terms of financial impact and loss of image
- Update company policies, procedures, standards and guidelines as needed
- Determine who initiated the incident for possible criminal and/or civil prosecution


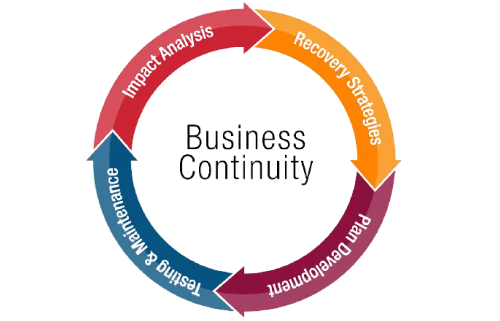
Is your SaaS Business Resilient?
We provide Business Impact Assessment (BIA)-as-a-Service
BIA Service Objectives
- Our Services will identify and evaluate critical technology infrastructure, software and data assets that support your key business processes and operations.
- We will assess impact to these critical assets in the event of a disruption from external, internal events or Cybersecurity Incidents.
- We conduct a Business Impact Assessment (BIA) and develop a Business Continuity and Technology Recovery Plans for your business.
Identity & Access Management (IAM)
We help you implement Identity and Access Management (IAM) processes that helps you securely control access to your systems and information resources and assets. Our objective is to ensure secure configuration of IAM Tools and supporting control processes to understand who is authenticated (signed in) and authorized (has permissions) to use your business network, systems, information resources and assets.
Threat & Vulnerability Management
Our Threat & Vulnerability Management service offering helps you business identify, evaluate, mitigate, and report on known security threats and vulnerabilities you business is exposed to. We prioritize and help you address possible and probable threats to minimize the "attack surface."
Threat Hunting & Incident Response Management
Automate your Security Operations and Incident Response Management with MDR, EDR and XDR Solutions to provide comprehensive protection from a wide range of threats to your endpoints, network, users, and cloud workloads through continuous and automated monitoring, analysis, detection, and remediation.
Security Culture & People
Security Culture highlights the values shared by individuals involved in an organization. This guides people with regards to their approach and actions that affect the security of the data of a company. With this, individuals feel more involved in preserving the data security of an organization. Security Awareness & Training campaigns are key to creating and sustaining a Security Culture in your organization.
Third-Party Risk Management
Our Virtual CISO (vCISO) Services help you manage Third-Party security and supply chain risks affecting your organization. Third-party risk management is now a requirement for organizations to protect their reputation, intellectual property, data, and competitive advantage. Increased reliance on third-party vendors and dependence on sub-processors means a broader attack surface and the spread of vulnerabilities & infections.
Risk & Compliance Reporting
A risk register is a list of project risks within an organization’s system. It allows companies to identify risks and document information about their nature. A risk report is a summary of this information, including threats, which helps an organization to create proactive decisions to manage risks. At IRM Consulting & Advisory we offercybersecurity consulting services for the above processes and we help you implement them.
If you are interested in our services, please set an appointment with us so we can thoroughly discuss your needs.
Download DatasheetOur Blogs
Quantum Computing and Cybersecurity
ISO42001 Certification Readiness Checklist
AI-Driven Autonomous Cyber Defenses
Our Industry Certifications
Our diverse industry experience and expertise in AI, Cybersecurity & Information Risk Management, Data Governance, Privacy and Data Protection Regulatory Compliance is endorsed by leading educational and industry certifications for the quality, value and cost-effective products and services we deliver to our clients.





%20(convert.io).webp?u=https%3A%2F%2Fimages.ctfassets.net%2Fbicx998lc6bb%2F62fmxBNo11THsjOp2HukAE%2Fcfd95ae76982266bb399ae48e77f9a8a%2Fai_risk_assessment__1___convert.io_.webp&a=w%3D750%26h%3D750%26fm%3Dwebp%26q%3D100&cd=2026-01-13T13%3A28%3A51.943Z)







