
Internet of Things (IoT) Security
Protect and secure data and information transmitted between sensors, connecting devices
and IoT Applications
What is IoT?
Internet of things (IoT) is a collection of many interconnected objects, services, humans, and devices that can communicate, share data, and information to achieve a common goal in different areas and applications.
IoT has many implementation domains like transportation, agriculture, healthcare, energy production and distribution. Devices in IoT follow an Identity Management approach to be identified in a collection of similar and heterogeneous devices.

Why is IoT Security Important?
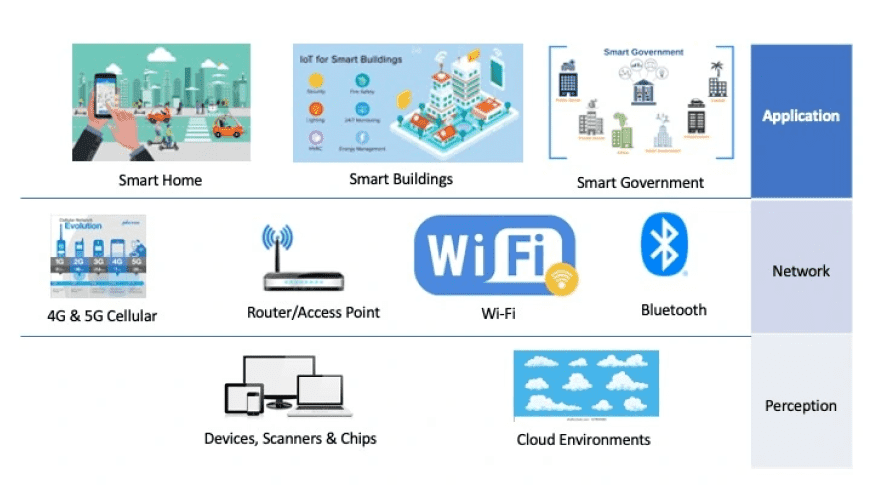
IoT mainly operates on three layers termed as Perception, Network, and Application layers. Each layer of IoT has inherent security issues associated with it.
Perception Layer
The Perception Layer is also known as the “Sensors” layer in IoT. The purpose of this layer is to acquire the data from the environment with the help of sensors and actuators. This layer detects, collects, and processes information and then transmits it to the network layer. This layer also performs the IoT node collaboration in local and short-range networks.
Network Layer
The Network Layer of IoT serves the function of data routing and transmission to different IoT hubs and devices over the Internet. At this layer, cloud computing platforms, Internet gateways, switching, and routing devices etc. operate by using some of the very recent technologies such as Wi-Fi, LTE, Bluetooth, 4G or 5G etc. The network gateways serve as the mediator between different IoT nodes by aggregating, filtering, and transmitting data to and from different sensors.
Application Layer
The Application Layer guarantees the authenticity, integrity, and confidentiality of the data. At this layer, the purpose of IoT or the creation of a smart environment is achieved.
IoT Security Threats
- IRM Consulting & Advisory focuses on each IoT layer that is susceptible to security threats and attacks. These can be active, or passive, and can originate from external sources or internal network owing to an attack by the Insider
- An active attack directly stops the service while the passive kind monitors IoT network information without hindering its service. At each layer, IoT devices and services are susceptible to Denial-of-Service attacks (DoS), which make the device, resource or network unavailable to authorized users.
- Typical security goals of Confidentiality, Integrity and Availability (CIA) also apply to IoT. However, the IoT has many restrictions and limitations in terms of the components and devices, computational and power resources, and even the heterogenous and ubiquitous nature of IoT that introduce additional concerns.
IoT Security Challenges
Our cybersecurity services addresses IoT challenges in two borad classes: Technological challenges and Security challenges. There are different mechanisms to ensure security including but not limited to:
- The software running on all IoT devices should be authorized.
- When an IoT device is turned on, it should first authenticate itself into the network before collecting or sending data.
- Since the IoT devices have limited computation and memory capabilities, firewalling is necessary in IoT network to filter packets directed to the devices.
- The updates and patches on the device should be installed in a way that additional bandwidth is not consumed
Talk to our Cybersecurity Trusted Advisor’s to learn how you can effectively mitigate these Security Threats and Risks.
Download Datasheet
Our Blogs
Quantum Computing and Cybersecurity
ISO42001 Certification Readiness Checklist
AI-Driven Autonomous Cyber Defenses
Our Industry Certifications
Our diverse industry experience and expertise in AI, Cybersecurity & Information Risk Management, Data Governance, Privacy and Data Protection Regulatory Compliance is endorsed by leading educational and industry certifications for the quality, value and cost-effective products and services we deliver to our clients.





%20(convert.io).webp?u=https%3A%2F%2Fimages.ctfassets.net%2Fbicx998lc6bb%2F62fmxBNo11THsjOp2HukAE%2Fcfd95ae76982266bb399ae48e77f9a8a%2Fai_risk_assessment__1___convert.io_.webp&a=w%3D750%26h%3D750%26fm%3Dwebp%26q%3D100&cd=2026-01-13T13%3A28%3A51.943Z)






